When computers first came onto the scene, applications and data storage was mostly conducted on the computer itself. At that time, if you wanted to store data on another computer (because you wanted to share it or wanted a back-up in case of an accident) the only way for most users to store items on something other than the computer’s hard drive was via portable storage. First the floppy disk, through CD-ROMs, to the multitude of options we have today such as USB sticks.
But through the internet, we were able to send & receive files even without saving to a USB stick. From there, the evolution continued with the ability to store and retrieve files on someone else’s servers, with on-demand access to download. We’re able to back-up our files on Dropbox, iCloud, and Google Drive; our phone’s photos are automatically saved too; and most organisations now have some online back-up capability in case anyone loses their laptop!
Now even the applications are stored on remote servers. Instead of asking employees to download lots of applications onto their computer, companies now give logins to online applications. Instead of having rooms & rooms of servers to run the website & business processes, companies now use “cloud” providers to do the heavy lifting and users can access anything they need over the internet.
Broadly put, when we say cloud computing, we mean delivery of computing processes over the internet.
On the face of it, cloud computing also feels like it should be more secure – I’m less reliant on my own hardware’s reliability, I don’t need to worry about maintaining my infrastructure, and my data is secured by the best minds in a leading tech company.
But the landscape isn’t so simple, and these advantages can lead to complacency. As is often the case, “out of sight, out of mind” isn’t an acceptable approach when key processes and customer data are at stake. Moving infrastructure to the cloud just changes the security considerations of which you need to be aware. Generally, those relate to the integrity of the provider you choose, managing user access to your cloud, and keeping track of all the different cloud tools your organisation is using.
Outsourced data
Firstly, now that you’re reliant on 3rd parties, you should be aware of their security considerations. Just as putting your valuable items in the Hatton Garden’s safety deposit boxes might be safer than keeping them in your bedside table, it doesn’t mean that they’re safe from theft. Similarly, putting your data and applications onto a cloud provider’s infrastructure might be safer than keeping on-site, but doesn’t guarantee it’s free from loss – responsibility now lies with the cloud provider.
It’s important to rigorously assess the security of any cloud providers you use, as well as making use of their in-built security settings to ensure your data is as safe as it can be. This is especially relevant in the post-GDPR world. As a data-handler, it’s ultimately your responsibility to confirm that your data controllers are GDPR-compliant, and to take reasonable precautions to safeguard your users’ data.
Access management
So, you’ve made sure you’re using a secure provider, with strong protection for your data – what’s next? Now time to ensure that this precious data can only be accessed by those who absolutely need to. In the old, cloudless world, an attacker would need to have a computer in the building to be able to access your company assets. Now, insecure credentials or misconfigured permissions are all anyone needs to get into your organisation. If access to your cloud infrastructure is not well-managed, then it’s just as insecure as if you’d left the door to your office open, or left access cards on the pavement outside the office building.
Managing access to your cloud infrastructure is essential – but thankfully it’s all about doing the basics well. Ensure that permissions for cloud services are configured to restrict access to only those who need it. Require members of your organisation to use strong, unique passwords, and multi-factor authentication where possible. Additionally, making sure you regularly review who’s accessing your cloud applications and what they’re doing (i.e. looking at the logs) will help you spot areas where you can make access to your cloud infrastructure even more secure.
Tracking
Finally, because cloud computing does away with the need for IT to set-up complex hardware & install applications, organisations have seen an explosion in the number of cloud service tools they use. This “shadow IT” covers the entirety of the business, with sales, marketing, HR, recruiting and other departments all making use of online apps to make their day-to-day work a little easier. However, this runs the risk of your organisation making use of insecure tools, and not appropriately managing access to the user data that’s being uploaded to these cloud providers. It only takes the weakest link to lead to a serious data breach, for which the whole organisation will be responsible.
Just as it’s important to make sure your enterprise cloud partners are secure, it’s essential to track the cloud tools that your organisation is using – first to confirm that there’s no overlap of existing solutions; but more importantly, to ensure that all integrations are appropriately secured.
Luckily, KYND can help
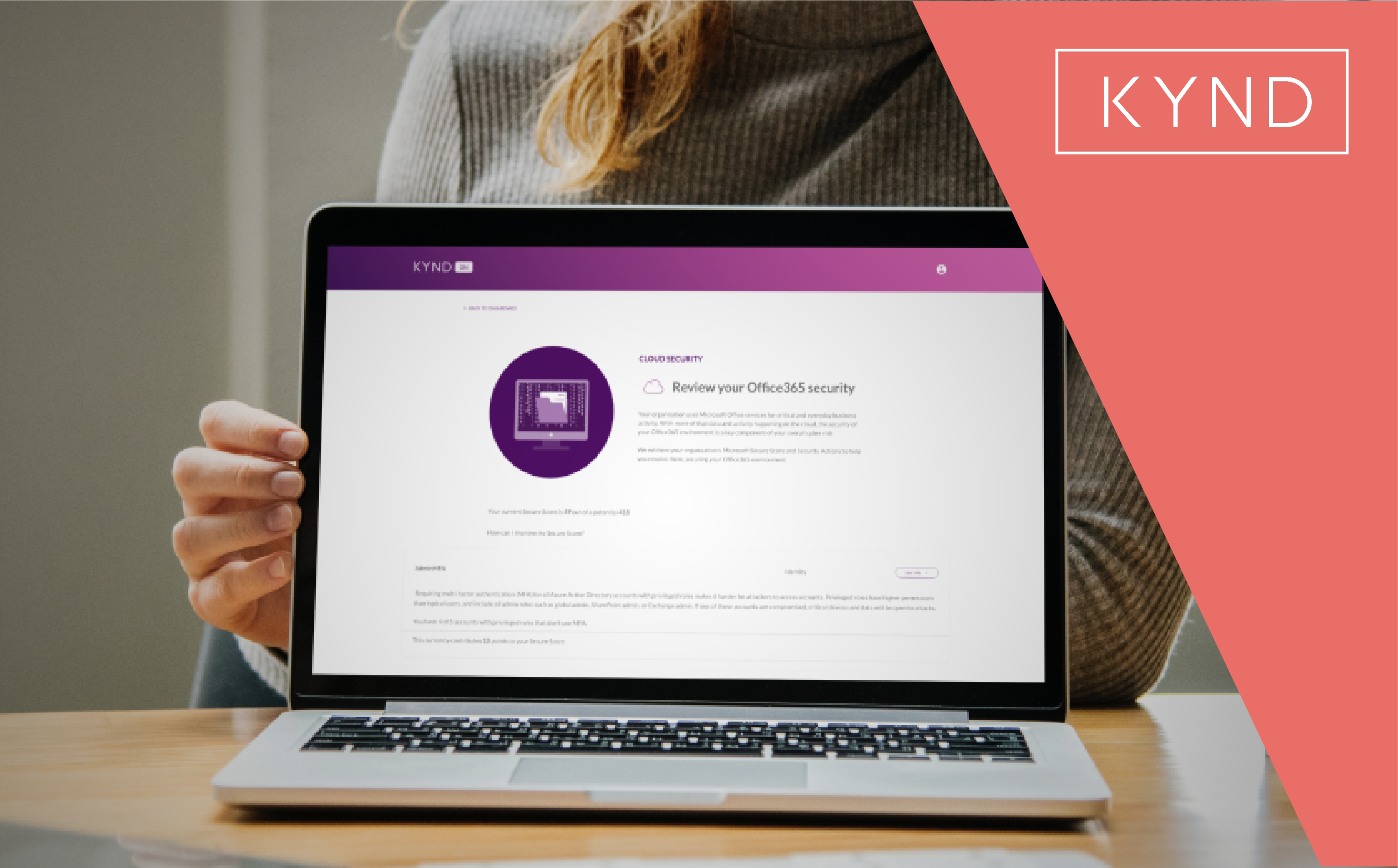
Thankfully, KYND makes these and other risks easy to understand, manage & fix. KYND ON now integrates with your organisation’s Office 365 cloud environment to retrieve recommended security actions across all your Microsoft apps. This is in addition to the service assessments that were already conducted on services we could connect to your organisation!
Microsoft’s Secure Score automatically marks the security of your cloud environment based on your organisation’s settings and usage – taking into account the specific tools & products your organisation uses. It also highlights the concrete actions you can take to improve this security score, spanning the full range of your Office 365 environment. For instance, enforcing multi-factor authentication for admins will minimise the chance of unauthorised access by attackers; enabling mailbox auditing will reduce the impact of any cyber incident affecting your Outlook; or enabling Safe Links will prevent your users from accidentally clicking on malicious links in files. The great thing is that the recommendations you receive are targeted and personalised for your organisation’s exact circumstances.
So where does KYND come in? Once you log in to KYND ON, you can now simply click “connect” on the cloud security page, and we’ll let you log in to Office 365. KYND will then do all the technical stuff to retrieve your Secure Score and recommended actions. They’ll then be consolidated in KYND, alongside all of your other cyber risks so you can address them all in one place. You can now start to take control of the risks involved with moving enterprise applications into the cloud, and KYND’s here to help you along the way. Get in touch if you’d like to find out more about how KYND can help you manage your cyber risks.
Share this article
Join the newsletter