
PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global
Understand, manage and take control of your organisation’s cyber risks simply, quickly and cost effectively.
Sell and renew more cyber insurance policies, and keep your clients happy with our tools and support.
Make better underwriting decisions by removing complexity and accessing instant insight into cyber risk exposure.
Get a clear, easy-to-understand view of cyber vulnerabilities and deliver real results for your clients.
Get a clear, easy-to-understand view of portfolio cyber risk vulnerabilities and minimise investment risk exposure.

By KYND


We’re now well into the pandemic and we have seen seismic changes in society, uprooting ideas we once held as principle - avoiding social contact, hybrid/remote working and consumption moving online. To adapt to this new world, businesses have been accelerating their digital transformation, moving their infrastructure to the cloud, and outsourcing services.
However, with this move to a digital landscape, the risk and impact of cyber attacks is only evolving and expanding in scope.
There are many reasons why individuals and organisations mistakenly believe their risk is low, and that this couldn’t possibly happen to them:
To help you better understand the risks, we’ve compiled this list of common myths and misconceptions about cyber attacks, and will explain why it’s best not to fall into them!
We’ve all seen the gamut of headlines where large enterprises have been targeted by cyber attacks, had their data breached or been held for ransom. As a result, there is a common misconception amongst some organisations that they’re too small to be a cyber target. This myth is fuelled by the natural focus of news stories being on large scale attacks on multinational corporations known to the public e.g. Bombardier, Apple, and Accellion.
While these eye-catching cyber attacks reverberate globally, they obfuscate the risks to the soft underbelly of the internet: small and medium-sized enterprises (SMEs). Little known is the fact that most cyber attacks aren’t targeted at specific companies – instead, 54% of cyber attacks are from automated tools casting a wide net across the public internet to find vulnerable hosts and ports.
Indeed, the statistics from independent and government reports on attacks make clear that SMEs are a significant target.
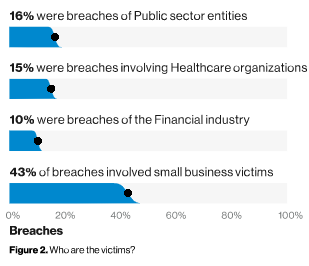
These statistics pour cold water on the notion that cyber criminals only target large enterprises, or that criminals will deliberately ignore smaller or non-profit-making organisations. In fact, the risks for SMEs are likely higher as there are no dedicated cyber security teams/departments at hand as there are in much larger organisations.
While all organisations, irrespective of size or industry, are at risk from cyber threats, this doesn't mean they’re an inevitability. There are measures which can be taken to prevent and mitigate such risks. The first step to a more secure digital future is to admit that you might be at risk, and then to take action to remedy it.
Some businesses may be inclined to feel that their data is not valuable, or that it is simply not worthwhile to a potential attacker.
However, almost all organisations will hold some client/customer data, internal records and communications, sensitive employee details, financial records, and operational systems. These are are all simple data items which a business requires to be functional, and without which it could not operate. If you imagine a scenario where this data isn’t available, would you be able continue business as usual?
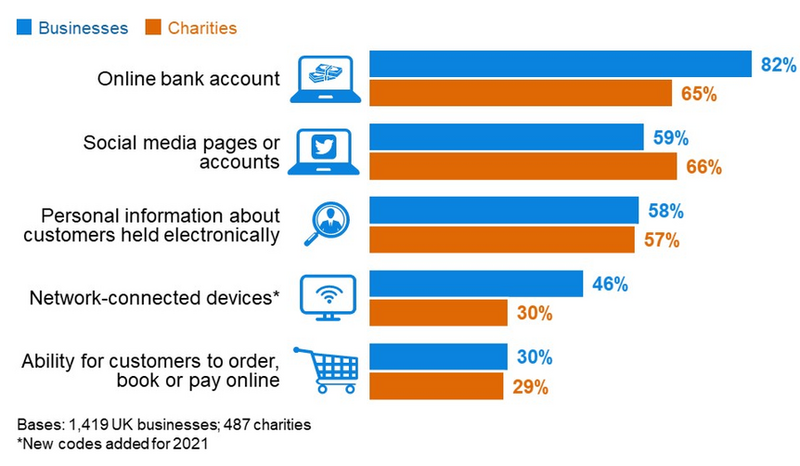
The chart above illustrates the digital footprint of organisations and their reliance on technology for basic functions. A successful cyber attack would likely render these unusable, or alternatively compromised - meaning that they could be used for fraud or other malicious purposes.
In the current environment it is common for cyber attackers to deploy ransomware to vulnerable systems, spread throughout the network and encrypt all data on infected machines, which can then be held for ransom. Where operational systems have been compromised, this would mean downtime.
The risks of a cyber attack cannot be understated, as the costs are significant - not only encompassing the direct financial loss but also regulatory fines (e.g. GDPR), trust and reputation loss, and the lost business and operational impact from downtime.
Data is valuable, whether it’s personal or for business operations, and should be protected as such. We’re not saying you need to become Fort Knox to protect data, there are sensible proactive measures which can be taken to effectively mitigate risks:
Symantec, which invented commercial software to protect computers from hackers, declares antivirus as 'dead.' http://t.co/H5lA3BmJO4
— The Wall Street Journal (@WSJ) May 11, 2014
A decade or two ago, the traditional antivirus in conjunction with a firewall was seen as adequate protection for system security. Though time and the sophistication of cyber attacks have advanced since then, the idea that the traditional antivirus is enough has persisted. Even Symantec (one of the world’s leading antivirus companies) themselves no longer feel that a simple antivirus is enough.
While antivirus will play a part within an organisation’s overall cyber security, it is not sufficient. The role of the traditional antivirus is to defend against known malware threats, but it cannot defend against threats it cannot identify. Indeed, around half of organisations have identified exploits and malware evading their antivirus solution.
The cyber threat landscape is fluid and ever changing, with complexity of malware and volume of attacks continually growing. To stay safe in this environment, organisations must adapt to this flow or else they risk being swept away by the tides.
Investing in an endpoint protection solution (examples include CrowdStrike, SentinelOne, CybeReason, Carbon Black) will allow your organisation to protect your devices (often called “endpoints”). These are also called ‘Next-Generation AntiVirus’ (NGAV) which supersede the traditional antivirus with a combination of artificial intelligence, behavioural detection, machine learning, and exploit mitigation, so that known and unknown threats can be anticipated and prevented.
Going further, planning and risk mitigation are vital to a good security posture. Starting with plans for incident response (how do we react when an incident occurs?) and business continuity (how do we keep our business operational when an incident occurs?) will provide a basis for future and ongoing planning and awareness. These can then be built on by the business, expanding to cover more areas and increasing the depth of your initial plans.
Cyber threats are often conflated with external threats, with high-profile attacks by external or nation-state actors naturally being more prominent. While this may appear true at first glance, there is substantial evidence which indicates that internal threats are significant and rising:
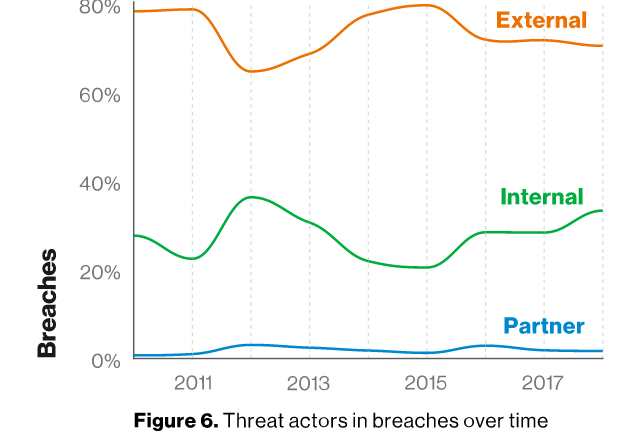
While the majority (69%) of attacks proved to be the work of outsiders in 2018, internal offenders involved themselves in a significant proportion (34%) of the incidents.
These statistics offer some sobering thoughts: cyber risks aren’t only external and could be executed from within the organisation. While this doesn’t mean that you shouldn’t trust your colleagues or partners at all, each device or endpoint should be treated as a possible threat – as if they could be malicious, or at least controlled by a malicious actor.
Internal attacks are not typically malicious, but are instead often accidental. Typically these are where data is sent to the wrong party. In the unusual scenario where there is a malicious internal attack, the intent is to disrupt operations and possibly to steal data and defraud the organisation. Such an attack is more effective due to insider knowledge and can cause major disruption including sensitive data leakage.
These potential risks can be mitigated through careful planning and compartmentalisation:
Having these measures in place substantially limit the exposure and impact of a successful cyber attack. An MDM solution is particularly valuable in this scenario as it would facilitate policies, controls and hardened configuration measures to be enforced without the chance for colleagues to mistakenly disable or misconfigure their device.
An underutilisation of IT or simply the lack of an IT department can often lead to a false perception that an organisation doesn’t have any IT, or that it doesn’t require IT to function.
However, if we stop to consider the reality, it’s difficult to imagine an organisation which doesn’t have any systems or networking; even the most offline of organisations. If the workplace is connected to the internet or there are any systems, including industrial systems, then the potential risk to cyber security exists.
A famous example is the Stuxnet virus, which targeted and destroyed Iran’s nuclear centrifuges and reduced their nuclear capability. These nuclear facilities were known to have no networking, however they did have industrial systems which could be targeted. While these were actions taken by nation-state actors, they highlight the risks clearly to even non-networked systems and how malware can adversely impact industrial systems.
In the case of an organisation which has limited IT infrastructure, core security measures previously mentioned will ensure that this doesn’t pose a risk to the rest of the business. These include implementing a “hardened” operating system configuration (particularly disabling auto-play and USB devices); drafting an incident response plan; and backing up core data separate from your network, ideally encrypted and protecting access with multi-factor authentication.
Another common myth is that cloud providers take care of cyber security. While this is true to an extent as these advanced providers protect their own infrastructure, this does not extend to content & services hosted on the platform itself, or to the configuration or setup of that infrastructure.
Each customer organisation is tasked with managing their own content/services and their own configuration, which includes cyber security management. This leaves your organisation to manage the ports, services, firewall rules, and other endpoints which could potentially be vulnerable.
Managing cyber security risks in this case will require knowledge and competence with the technologies offered by the cloud provider in order to secure them. While the particular settings for each cloud-provided service will vary, there are some typical checks which should be carried out when deploying to a cloud environment:
At the heart of security it’s not necessarily who you are, or what products you use, but the configuration of your infrastructure, devices and network which is the primary factor in determining and mitigating risk. That is, you’re only as secure as your configuration.
Here at KYND, that’s what we focus on. We’ve developed pioneering technology that makes cyber risks simple to understand, quick to monitor and easy to prevent. Our aim is to stop cyber risk affecting any business, big or small, basic or advanced. If you’d like to find out more or see a demo, get in touch and we’d love to chat.

PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global

PRESS RELEASE: Talan chooses KYND to deliver advanced cyber risk intelligence to clients

PRESS RELEASE: KYND wins ‘InsurTech Innovation of the Year’ at InsuranceERM Americas Awards 2025
Accreditation & Features