
PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global
Understand, manage and take control of your organisation’s cyber risks simply, quickly and cost effectively.
Sell and renew more cyber insurance policies, and keep your clients happy with our tools and support.
Make better underwriting decisions by removing complexity and accessing instant insight into cyber risk exposure.
Get a clear, easy-to-understand view of cyber vulnerabilities and deliver real results for your clients.
Get a clear, easy-to-understand view of portfolio cyber risk vulnerabilities and minimise investment risk exposure.

By KYND


The Novel Coronavirus (or COVID-19) is directly affecting people and businesses around the globe. Amid all the turmoil, the bad actors out there are capitalising on the chaos to exploit the unwary and vulnerable.
This seems to be primarily happening in two ways.
Firstly, by exploiting fears about the spread of Coronavirus through phishing scams.
Secondly, the huge increase in people working from home means the use of remote working technology such as Remote Desktop Protocol (RDP) soars. RDP, when set up correctly, is a great tool for remote working. However, hackers are using it as a gateway exploiting vulnerabilities on insecure or incorrectly set up RDP servers. Even worse they are using it as a means to distribute new and highly sophisticated versions of ransomware.
As businesses worldwide are adapting their ways of working to continue to operate in the face of a global health emergency, various COVID19-related tactics and phishing campaigns have been uncovered that are leaving companies vulnerable.
Below, we've rounded up some examples of the latest scams and remote working vulnerabilities that you should be aware of to nip the threats in the bud and keep yourself and your business safe.
Hundreds of people have received a very convincing email with a GOV.UK header claiming that the government has established a new tax refund programme "as a precautionary measure against COVID-19 in cooperation with the National Insurance and National Health Services", and encouraging the recipient to click the provided link to get the money they're owed as their tax rebate.
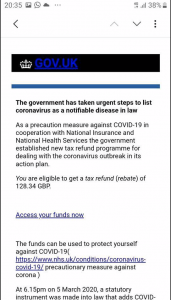
The link redirects them to a fraudulent website with an HMRC logo, that asks for the victim's personal and financial information and then subsequently passes all the necessary information to the fraudster. Happy days (for the fraudster indeed)!
And while it's tempting to follow the link - simply keep in mind that genuine organisations like HRMC or banks would never contact you directly out of the blue asking for your personal or financial information over text or email, including for a tax refund. We also recommend checking the GOV.UKwebsite for information onhow to avoid and report scams and to recognise genuine HMRC contact. So whether it's a very promising email, text message or a phone call - please refrain from clicking on the links or attachments in suspicious emails and never respond to unsolicited messages, texts and calls that ask for your personal or financial details.
Another Coronavirus phishing email has been targeting employee's work email accounts whilst businesses are proactively implementing safety measures to counter Coronavirus in the workplace. Malicious emails include a 'working from home' announcement to employees, along with a link for more information that appears to be legitimate.
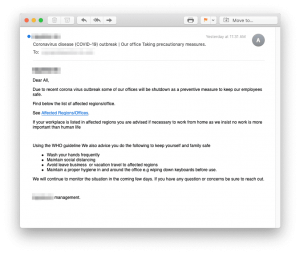
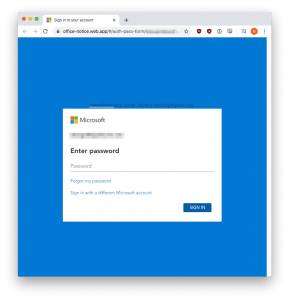
Once a user clicks on the links, he/she is taken to a phishing website that appears to be owned by Microsoft and asks to login. When a victim enters their credentials, the information will be saved for the phishers to retrieve later so that they can compromise the victim's business email, confidential business information, customer data, and more. Most tips for this will remain the same as for standard cyber awareness: keep your staff up-to-date on the different types of emerging email scams, look closely at the email address a message is sent from, be wary of clicking links and attachments, and simply keep an eye out for things that don't seem right.
Scammers are posing as authorities like the World Health Organisation or Centreer for Disease Control in order to trick individuals into handing over their personal information to get a path to the company's assets.
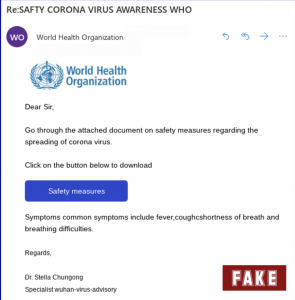
As a general rule here, never share your personal or financial information via email or message. And always verify the source before acting on any news about COVID-19 and its impact on your business. We also recommend visiting the official website or social media channels for the latest advice.
For those who use Gmail/GSuite in their organisations, we’ve also created the Free KYND Gmail Email analyser. Now you can easily and quickly check the SPF, DKIM & DMARC status of emails you receive, and the SPF & DMARC settings of your own domain to prevent your organisations’ being spoofed. As you may have noticed, at KYND we’re big believers of prevention being better than cure.
As the Novel Coronavirus outbreak continues to spread, more and more companies are asking their employees to work from home, which adds extra pressure to the red-hot security situation. RDP, if not properly configured and secured, can act as a gateway within a business for the crooks to access corporate systems and sensitive data. To add some more woes to it, our recent KYND research shows that 20% of the AIM companies currently have their RDP ports open to the internet, which automatically makes them a potentially vulnerable target for ransomware attacks like SamSamor CrySIS that is all being spread through the RDP’s weak spot.
Additionally, hackers are using new and sophisticated ransomware such as Nefilim which threatens to release stolen data. In the Nefilim ransom note, the attackers state that if a user does not pay the ransom in seven days they will release data that was stolen from the network.

In the past, this would have been seen as an empty threat, but now the technology to enable this extraction exists and we have seen hackers following through with their threats. It should no longer be ignored.
Therefore, it's essential for organisations of all sizes and types to set up processes to enable their staff to connect remotely, securely. Businesses can help to protect their employees by ensuring anyone who connects to their network uses a VPN, that their remote access tools are secure and up-to-date, and that a multifactor authentication (MFA) is implemented to support traditional password authentication. We know we're repeating ourselves, but it's better to be safe than sorry.
If you’re worried about how the risks of the enforced remote working might pose to your business, KYND ON can help! It will quickly show you the areas where your business can potentially mitigate the existing risks and give you peace of mind. At KYND, we’re dedicated to making cyber risks simple to understand, quick to monitor and easy to prevent. So don’t leave your cyber risks to chance -get in touch to see how KYND can help you. And may both you and your business stay safe and secure!

PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global

PRESS RELEASE: Talan chooses KYND to deliver advanced cyber risk intelligence to clients

PRESS RELEASE: KYND wins ‘InsurTech Innovation of the Year’ at InsuranceERM Americas Awards 2025
Accreditation & Features