
PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global
Understand, manage and take control of your organisation’s cyber risks simply, quickly and cost effectively.
Sell and renew more cyber insurance policies, and keep your clients happy with our tools and support.
Make better underwriting decisions by removing complexity and accessing instant insight into cyber risk exposure.
Get a clear, easy-to-understand view of cyber vulnerabilities and deliver real results for your clients.
Get a clear, easy-to-understand view of portfolio cyber risk vulnerabilities and minimise investment risk exposure.

By KYND


In today's digital landscape, cyber threats have become an inevitable reality for businesses worldwide. However, the shocking MOVEit data breach has left the world astonished due to the unprecedented scale of its impact amongst businesses and the alarming volume of sensitive information now under the control of hackers. This disastrous event has once again highlighted the grave consequences of cyber attacks, showcasing how easily it can send businesses into a whirlwind of chaos.
This blog delves into the details of the recent MOVEit data breach, its effects on businesses’ sensitive data and reputational image, and the importance of proactive cyber risk management tools which could have prevented the attack from happening in the first place.
So what exactly happened? Well, MOVEit, a popular file transfer and secure messaging platform, was targeted in a highly sophisticated cyber attack in early June 2023. A notorious cyber gang known as Clop, suspected to operate out of Russia published a blog post announcing their successful infiltration of worldwide MOVEit transactions. They issued an ultimatum urging organisations utilising MOVEit to reach out to them before June 14 to discuss ransom terms. Failure to comply would result in the public disclosure of the stolen information.
Why a blog and not a direct email like the majority of ransomware attacks? Experts believe that it’s due to the enormous number of victims with data on the MOVEit systems. The full blog post reads:
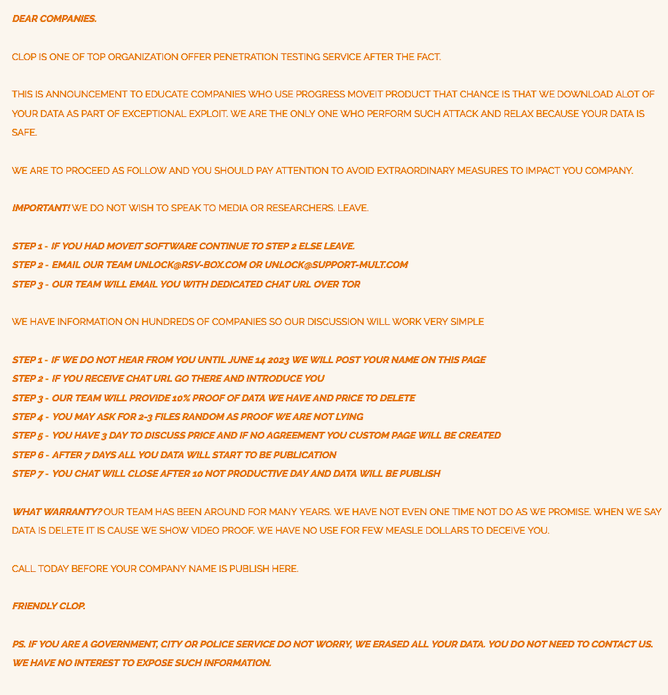
The attackers exploited a zero-day vulnerability, a previously unknown software flaw, allowing them to gain unauthorised access to users’ sensitive information. This security gap was mass-exploited, resulting in widespread data theft across various industries. The attackers gained access to the MOVEit platform and exfiltrated valuable data. The breach compromised the confidentiality and integrity of the stolen data, leaving organisations exposed to the risk of identity theft, financial fraud, and potentially long-lasting reputational damage.
The consequences of the MOVEit data breach are far-reaching and devastating for the affected businesses. Stolen data includes personally identifiable information (PII), financial records, and confidential documents, leaving organisations completely exposed. At the time of writing, the aftermath of the breach is still unknown, however, if history is anything to go by, it could result in substantial financial losses due to legal liabilities, regulatory penalties, and the cost of remediation efforts. Additionally, the loss of customer trust and confidence could have a profound impact on brand reputation, potentially leading to customer churn and revenue decline.
So, what lies ahead for the affected businesses? Unfortunately, they are left with only two unfavourable options: refusing the ransomware demand and risking the release of their sensitive information online, or paying the ransom and relying on the word of these professional bad actors that they will delete the information. However, given the nature of these attackers, it is impossible to ascertain whether they will genuinely delete the information after receiving the payment. A specialist insurer at Hiscox found that 36% of companies who opted to pay the ransom after a data breach were targeted a second time. One thing that can be certain is that businesses must now be more vigilant and aware of the vulnerabilities they are susceptible to.
The MOVEit data breach serves as a wake-up call for organisations to prioritise cybersecurity. Several lessons can be learned from this incident:
Zero-day vulnerabilities: The exploitation of a zero-day vulnerability underscores the need for continuously monitoring robust cyber risk management practices. Regular security audits, patch management, and proactive threat intelligence can help identify and mitigate such vulnerabilities.
Third-party risks: The breach through MOVEit highlights the importance of thoroughly vetting and monitoring third-party vendors. Organisations should implement strict security requirements and perform regular assessments to ensure the security of their supply chain.
Incident response readiness: The ability to detect, respond, and contain a cyber attack is crucial. Organisations should have well-defined incident response plans, regular training, and simulations to effectively handle security incidents and minimise their impact.
To prevent and mitigate these devastating consequences of cyber attacks, organisations must adopt proactive cyber risk management solutions in order to prevent zero-day attacks. That’s where KYND comes in, offering a streamlined and expedited discovery process. With our advanced technology and expertise, we swiftly identify these vulnerabilities, ensuring prompt notification to affected clients along with tailored remediation advice for the vulnerable product. Some of the preventative measures KYND provides are:
Prioritised risk insights: KYND provides organisations with actionable insights that matter to them by putting risks in order of priority which allow them to mitigate threats before they have a chance to strike. KYND also provides cyber experts in order to consulate with businesses in order to assist them in mitigating their vulnerabilities.
Advanced monitoring: KYND’s advanced monitoring proactively scans for the most critical exploits that are known to be actively exploited by attackers affecting organisations today, making it easier to identify and manage the cyber risks affecting an organisation.
Continuous cyber risk monitoring: KYND continuously scans and monitors an organisations’ digital footprint, identifying vulnerabilities, misconfigurations, and exposure to cyber threats across the supply chain.
The MOVEit data breach is just one example of a zero-day vulnerability wreaking havoc on businesses, and unfortunately, it won't be the last. Every hour of every day, malicious actors are tirelessly attempting to exploit any vulnerability in order to gain access to sensitive information. Given this reality, it may seem like the battle is already lost, and businesses should simply accept this inevitability. However, the General Data Protection Regulation (GDPR) doesn’t allow this option to be viable. Regardless of how a breach occurs, GDPR regulations impose fines of up to 4% of annual turnover on organisations that experience such incidents.
Of course, returning to the days of storing everything in physical filing cabinets is not a practical solution in the digital age. We have surpassed that stage long ago. While there is no foolproof method to eliminate all data breaches, it is possible to mitigate them by implementing robust internal security measures and comprehensive cyber risk management.
By staying vigilant in the face of evolving cyber threats, businesses can significantly reduce the risk of data breaches. As technology advances and cyber crime becomes more sophisticated, it’s crucial to adopt these types of proactive measures to protect sensitive information and mitigate potential damages.
By partnering with KYND, businesses can gain the necessary insights and tools to stay ahead of cyber threats, protect their sensitive data, and safeguard their reputation.
As the MOVEit data breach has demonstrated, it is no longer a question of if a cyber attack will happen, but when. Therefore, it is crucial for organisations to prioritise cybersecurity and invest in comprehensive risk management solutions like KYND.
Whether you’re an insurer seeking to provide these powerful capabilities to your insureds or a business aiming to enhance your protection against the ever-growing cyber threats, we encourage you to reach out to our team of friendly experts who will provide you with comprehensive information about our powerful cyber risk management services. Click here to get in touch with us today.

PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global

PRESS RELEASE: Talan chooses KYND to deliver advanced cyber risk intelligence to clients

PRESS RELEASE: KYND wins ‘InsurTech Innovation of the Year’ at InsuranceERM Americas Awards 2025
Accreditation & Features