
PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global
Understand, manage and take control of your organisation’s cyber risks simply, quickly and cost effectively.
Sell and renew more cyber insurance policies, and keep your clients happy with our tools and support.
Make better underwriting decisions by removing complexity and accessing instant insight into cyber risk exposure.
Get a clear, easy-to-understand view of cyber vulnerabilities and deliver real results for your clients.
Get a clear, easy-to-understand view of portfolio cyber risk vulnerabilities and minimise investment risk exposure.

By KYND


In today's fast-paced digital landscape, with numerous cyber threats emerging daily, the demand for cyber insurance has never been greater, and organisations are looking to minimise their risk exposure. For underwriters providing cyber coverage, the use of external vulnerability scanning tools – referred to as outside-in scans, where businesses’ potential external entry points for unwanted intrusion are identified – alongside the traditional application form to evaluate their clients cyber risk profile accurately and quickly, is growing rapidly.
Recently, however, the value of these outside-in scans to help underwriters accurately assess a company’s cyber risk profile has been challenged with a view that internal vulnerability scanning, where a scan is performed to identify a business’ internal network to identify at-risk factors, is potentially more valuable to underwriters. Is there any validity to this challenge? In this blog we’re going to delve deep into both scanning methods to find out!
Before we get deep into which scanning method matters for cyber underwriters and why, it’s worth briefly mentioning why cyber underwriters use vulnerability scanning methods in the first place.
Historically, underwriters have relied on application forms in order to assess a business’ risk profile. However, they can paint an unreliable picture as they oversimplify complex situations. When faced with binary options such as “yes” or “no”, when in reality the answer is “maybe” or “it depends”, insured IT managers tend to default to "yes” and provide an incomplete risk picture, leaving underwriters longing for more comprehensive and factual insights. This has severe consequences during claims adjudication, causing considerable disparities and resource drains for the industry.
Thankfully, with the advancement of technology, methods for accurately assessing an organisation’s cyber risk posture such as internal and external vulnerability scanning have helped to fill in the gaps and obtain a more complete picture.
So, what exactly are internal and external scans?
External scanning, also known as outside-in scanning, essentially refers to an underwriter conducting an external vulnerability scan on the websites, networks, and servers of a business in order to identify security weaknesses that could be exploited by cyber criminals from the outside, as a hacker would. This is a quick and usually non-intrusive approach to see a business’s vulnerabilities.
On the other hand, internal scanning, referred to as inside-out scanning, usually involves a “behind the firewall” approach where a business’s vulnerability assessment is performed with full access to the internal network that's being scanned to assess its susceptibility from the inside. These scans usually focus on things like workstations, servers and software that are located inside the organisation’s network borders, therefore the whole installation process can be long and costly as it requires many high level permissions. However, with the current global economic pressure and the softening cyber insurance market, this prompts underwriters to consider if a more thorough analysis on their data warrants cost savings and additional risk management value.
With these scanning tools now readily available to underwriters, they no longer need to rely on just the application process when making underwriting decisions. But that now begs the question: which one should underwriters be focusing more on? Well, in a nutshell, both are immensely important to understand a business’s risk posture. However, there are some points raised which suggest that internal scanning is the optimal choice for underwriters to uncover digital perils, but the real answer requires a little more digging.
It is widely recognised that a significant portion of a company's infrastructure, roughly 99%, exists within its internal systems, which cannot be easily captured through outside-in scans responsible for analysing the perimeter of an organisation’s network.
Contrary to external scans, internal vulnerability scans can penetrate the existing network for security vulnerabilities with a greater depth. However, there is a flip side. This approach presents a significant challenge for cyber underwriters who must sift through a vast amount of risk data to pinpoint actual threats to their portfolio. So the real question is, how extensively do cyber underwriters need to analyse an applicant's cyber posture to gather the tangible facts necessary for making informed, evidence-based decisions?
The answer may surprise you. Firstly, with more than 220,000 Common Vulnerabilities and Exposures (CVE) identified in the US National Vulnerability Database, and over 70,000 ranked as critical or high risk, only a small fraction (less than 4%) have ever been publicly exploited and, therefore, present a real threat to underwriters’ portfolios. The severity of an issue doesn’t necessarily correspond with its likelihood of being exploited; in the real-world, vulnerabilities stated as critical can be challenging to exploit and often require an extremely narrow set of conditions to take advantage of. That’s why many cybercriminals focus on exploiting medium or even low severity vulnerabilities instead that can be used to gather information or chain with other vulnerabilities to cause widespread negative impact on businesses, including those attempting to pass underwriting criteria in order to obtain much-needed cyber coverage. Again, this threat emanates from the above mentioned 4% of published CVEs that represent real risk for most businesses right now.
Moreover, one of the most difficult areas to comprehend and secure are external-facing assets in any organisation’s infrastructure. These are the assets and systems that are publicly accessible from the Internet – such as VPN gateways, DNS servers, Remote Desktop Access Services, web servers, email and other internet-facing systems – and it’s these factors that are the first things cybercriminals will look to compromise as they serve as a potential pathway to an organisation’s valuable data. Performing an external vulnerability scan would not only enable both an underwriter and their client to see exactly where the organisation’s most critical, immediate vulnerabilities are, but will allow the organisation to address those weaknesses before they turn into a successful security breach and subsequent claim in-life.
Going back to our original question, while internal vulnerability scans certainly offer a more comprehensive analysis of a business’s infrastructure, it’s important to note that only a small number of vulnerabilities necessarily present a significant risk to businesses and subsequently underwriters (a good way to determine whether those vulnerabilities are external or internal would be to see what of the top EPSS percentile CVEs are network versus local). The key lies in directing attention towards the fraction of vulnerabilities that have the potential to pose a genuine and immediate threat to their portfolio. By prioritising these high-impact vulnerabilities, underwriters can make informed, evidence-based decisions to help their portfolio companies mitigate risks before they manifest as costly security breaches and subsequent claims.
As discussed above, cyber criminals predominantly exploit external methods to breach systems, targeting exposed infrastructure and external attack vectors. Now, in order to gain a better understanding of what exactly this means and how it works in practice, let's dissect some real-world cyber attack numbers and delve into their implications.
According to data from Coveware, email phishing accounts for approximately 32% of all ransomware attacks on enterprises over the course of Q4 2018 - Q1 2023, while RDP (Remote Desktop Protocol) compromise and software vulnerabilities make up around 25% and 18% respectively.
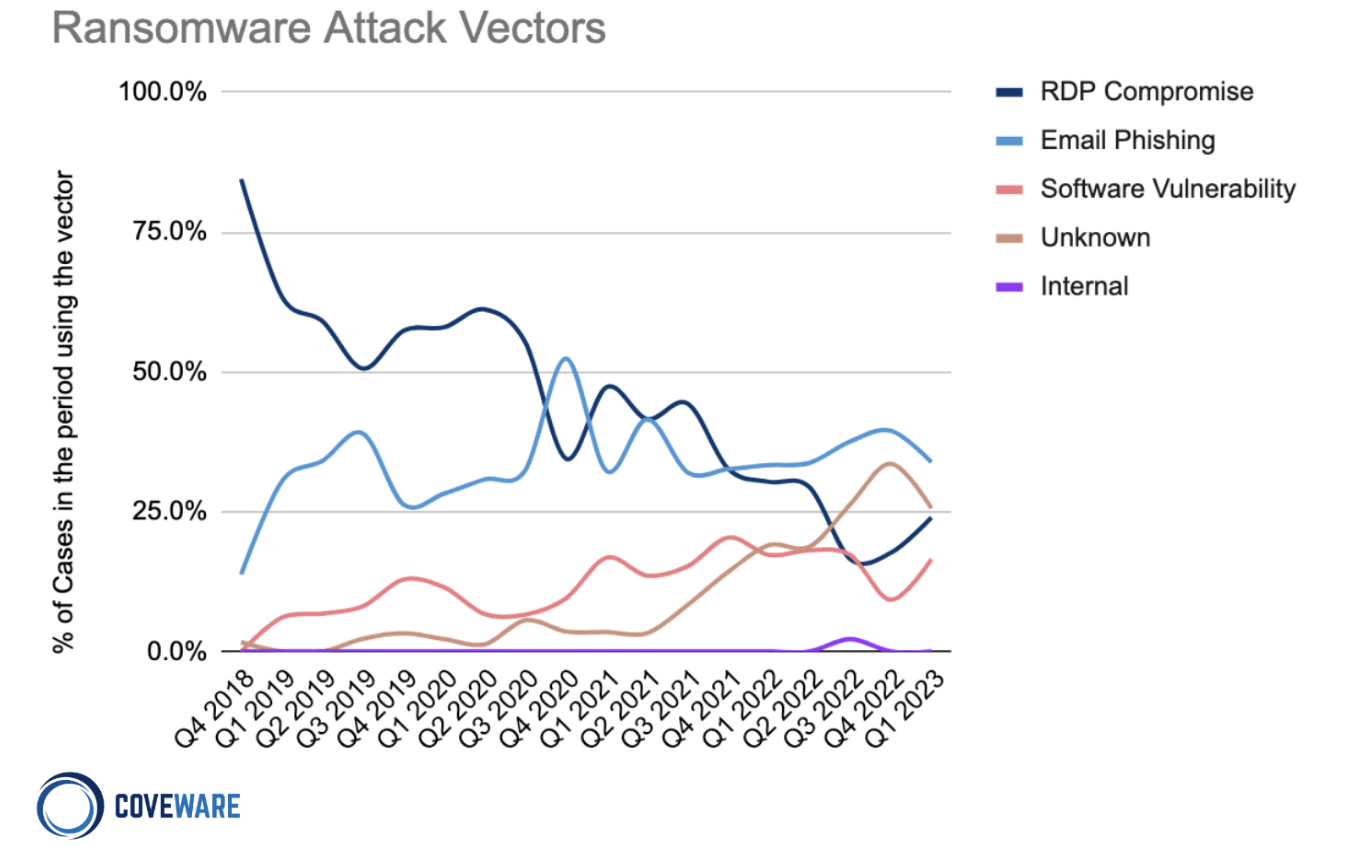
(Source: Coveware)
Further data from Beazley explores the latest trends in quarterly global claims, and data reveals an uncanny similarity in attack vectors when analysing ransomware incidents over the period of Q1 2020 - Q1 2023:
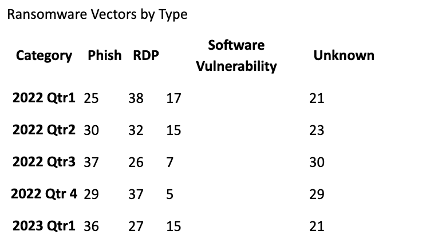
(Source: Beazley)
The captivating twist in this tale is that many of these measures can only be effectively and independently assessed looking at the business from the outside, covering approximately 43% [RDP and software vulnerabilities] of observed attacks in the Coveware data and 42% in the Beazley data respectively. But let's break down exactly what we mean by that and look at each of the vectors.
Software vulnerabilities in this context require specific attention. As we mentioned earlier, it’s only around 4% of the total number of CVEs that represent a real threat to organisations. Additionally, threat actors are quick to exploit these types of vulnerabilities, with 42% of known exposures being used on day 0 of disclosure, 50% within 2 days, and 75% within 28 days, making it crucial for underwriters to focus on priority attack vectors rather than getting overwhelmed by cataloguing all potential vulnerabilities. This revelation challenges the prevailing belief and prompts a reevaluation of standard approaches to cyber risk assessment for underwriters.
RDP exposure assessment is also nuanced. Many organisations will take advantage of load balancing technology and content delivery networks that can appear to offer RDP connections to the organisation’s infrastructure. These are false positives and can be dismissed from a risk assessment perspective, but this filtering needs to be based upon accurate discovery and mapping of the organisation's external infrastructure to ensure real risks are not dismissed in this filtering.
Enter email phishing: an organisation’s susceptibility to be being phished can be partially and independently assessed by looking at the protective measures that have been put in place, such as inbound email protection and domain spoofing protection using global open standards such as SPF, DKIM and DMARC. Of course, the susceptibility to the human factor in phishing is difficult to assess but that is no easier from inside the business. This is the reason why regular cyber security and phishing awareness training for all employees is vital and is covered in many cyber insurance proposal forms. Email phishing is also actively tested using non-invasive external scanning methods as teams send real world phishing emails and analyse data such as open rate and click rate to determine if an employee is susceptible to phishing attacks. This method can effectively allow underwriters to test the interior of a company from external without any permissions from inside governance.
Lastly, as the above mentioned statistics show, a specific attack vector could not be determined in 21% - 25% of cases. This inherent challenge stems from the constantly evolving nature of the threat landscape, and neither inside or outside risk assessments can help in this case.
The numbers above reveal the importance of external scanning when assessing cyber risk, as insurance carriers can gain visibility into the vulnerabilities that are exposed to the outside world and understand the potential entry points for cyber attacks before an overlooked loophole turns into a successful security breach.
With the right tools, the majority of these critical risk factors can be assessed pre-submission using external vulnerability scanning before they turn into a successful attack and, subsequently, a claim. While the amount of risk data underwriters can access today can be overwhelming, it’s all about getting the data you really need and making the most of it. This implies that while external scan data is not a silver bullet solution, it brings insurers closer to optimal underwriting outcomes.
Leveraging external scanning data in cyber underwriting processes shows it to be effective as insurers can now benefit from greatly improved risk insights into organisations’ cyber posture and the ability to deploy this capability efficiently and effectively at scale, allowing for mass-risk data analysis. Despite concerns about false positives, the benefits far outweigh the perceived issues, especially considering the zero-touch, fast, and efficient nature of this approach. Additionally, it does not disrupt the transactional nature of the cyber insurance purchase process.
Another important factor to consider is that internal scanning often requires the installation of monitoring software or enabling API connections within the business and its on-premises and-cloud hosted infrastructure which is not only a time-consuming and costly process for both underwriters and their clients, but it also requires the business to share sensitive internal access with a 3rd party company. Due to the changing attitude to internal scanning, insurers now incentivise "digital validation," allowing them to assess risk by observing the environment beyond the firewall. However, businesses hesitate to open their systems due to security concerns and potential impact on insurance coverage if their safeguards fall short of underwriting standards. All of this necessitates high-level permissions and cooperation from all parties involved.
This impresses the importance of outside-in scan data using technology such as KYND’s, which utilises external vulnerability scanning and automated discovery. In contrast to internal scanning, it offers a quick and easy evaluation of a business’s exposure through the eyes of cyber criminals with just a simple URL. This allows underwriters to get a robust understanding of a business’s cyber risk posture without the need for invasive internal installations. This effectively saves underwriters a significant amount of time and resources, while enabling them to effectively determine adequate policy coverage to insure their clients from a cyber attack.
As we discussed, although at first glance it may appear that external vulnerability assessments only reveal the tip of a vast cyber iceberg when assessing an organisation’s cyber posture, in reality, it equips cyber underwriters with precise and focused insights into business’ exposure, empowering them to navigate today’s challenging cyber threat landscape with confidence. By leveraging advanced risk intelligence such as KYND’s, cyber underwriters can:
Enhance risk assessment capabilities: External scans effectively enable underwriters to evaluate the security posture of businesses by identifying potential vulnerabilities and weaknesses in their external-facing systems. By understanding the vulnerabilities that could be exploited by cybercriminals, underwriters can accurately assess the level of risk associated with insuring a particular organisation and how likely a security breach is.
Drive risk intelligence-led underwriting decisions: The insights gained from external scanning assist underwriters in making better-informed underwriting decisions and tailor coverage, policy terms, and pricing based on the identified vulnerabilities and risks. This ensures that the policy adequately covers the specific cyber risks faced by the business, minimising potential coverage gaps or overestimation of risk.
Establish and maintain partnership in risk management: External vulnerability scanning promotes a collaborative partnership between underwriters and their clients in managing complex and ever-evolving cyber risks. By sharing the assessment findings, underwriters can actively engage with their clients in identifying and mitigating vulnerabilities. Additionally, this can reveal part of an organisation’s infrastructure which weren’t considered by internal teams (including development/test environments, or assets set & owned by other areas of the business). This collaboration fosters a proactive risk management approach and enhances the overall cyber resilience of the insured organisation.
Harness the power of continuous monitoring: Utilising continuous external vulnerability assessments provides ongoing monitoring, ensuring that cyber underwriters stay informed about changes in their portfolio’s cyber health. This enables them to adjust insurance coverage for their new/renewing customers and risk management strategies accordingly, keeping pace with evolving threats and reducing the likelihood of substantial losses.
With wide availability of both external and internal vulnerability assessment capabilities on the market, it’s important to remember that it’s not the quantity, but the quality of risk data that matters in cyber underwriting. The key lies in obtaining a comprehensive perspective by ensuring underwriters have access to the right data at the right time. While internal vulnerability assessments are undeniably important for generating full visibility into a company’s security posture, the majority of cyber attacks originate from external sources. This indicates that external vulnerability scanning provides an adequate and proactive approach to risk assessment, enabling underwriters to see the most prevalent risk factors likely to cause cyber incidents within their portfolio and mitigate losses.
KYND offers a comprehensive solution for underwriters to effectively evaluate their clients' risk posture, proactively identify vulnerabilities, ensure ongoing monitoring, and provide actionable remedial recommendations to their clients. By partnering with trusted cyber risk management companies like KYND, underwriters are able to quickly conduct a non-invasive scan by simply entering a business's URL in order to see their most critical cyber vulnerabilities in order of priority instantly, and allowing them to make evidence-based insurance decisions without high level permissions from their clients. Leveraging actionable insights into a business’s cyber risk exposures, underwriters can navigate the evolving threat landscape, improve their client’s risk posture in the rapidly advancing digital landscape, and keep their losses to a minimum.
If you want to find out how KYND's powerful technology can help take your cyber underwriting to the next level, please don’t hesitate to get in touch with our friendly experts here.

PRESS RELEASE: KYND named among world’s most innovative AIFinTech companies by FinTech Global

PRESS RELEASE: Talan chooses KYND to deliver advanced cyber risk intelligence to clients

PRESS RELEASE: KYND wins ‘InsurTech Innovation of the Year’ at InsuranceERM Americas Awards 2025
Accreditation & Features